I needed to ramp up on the new feature of AWS’s Managed Active Directory (Hybrid Edition) and so it’s good opportunity to share my experience.
First off the use case – much like the original version of Managed AD, the Hybrid Edition is ment to allow organizations to extend their on-premises AD to the cloud and leverege it to access cloud resources. Previous to Hybrid Edition, the options were to use Managed AD and create a trust or use the AD Connector.
As the name implies, Hybrid is bit different as it extends the on-premises forest/domain into the cloud with a new AD site. In my testing I spun up a single forest/single domain in VPC with two DC running on EC2, the Hybrid created a new AWS-DirectoryServices-us-west-2 site, in the same VPC (the second DC was still being created in the screenshot)
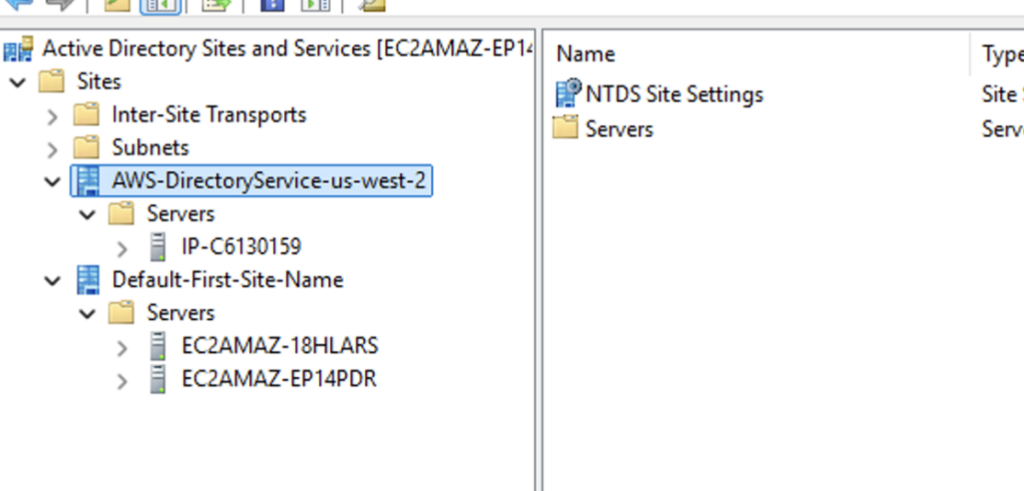
Along with the new site several GPOs are created:
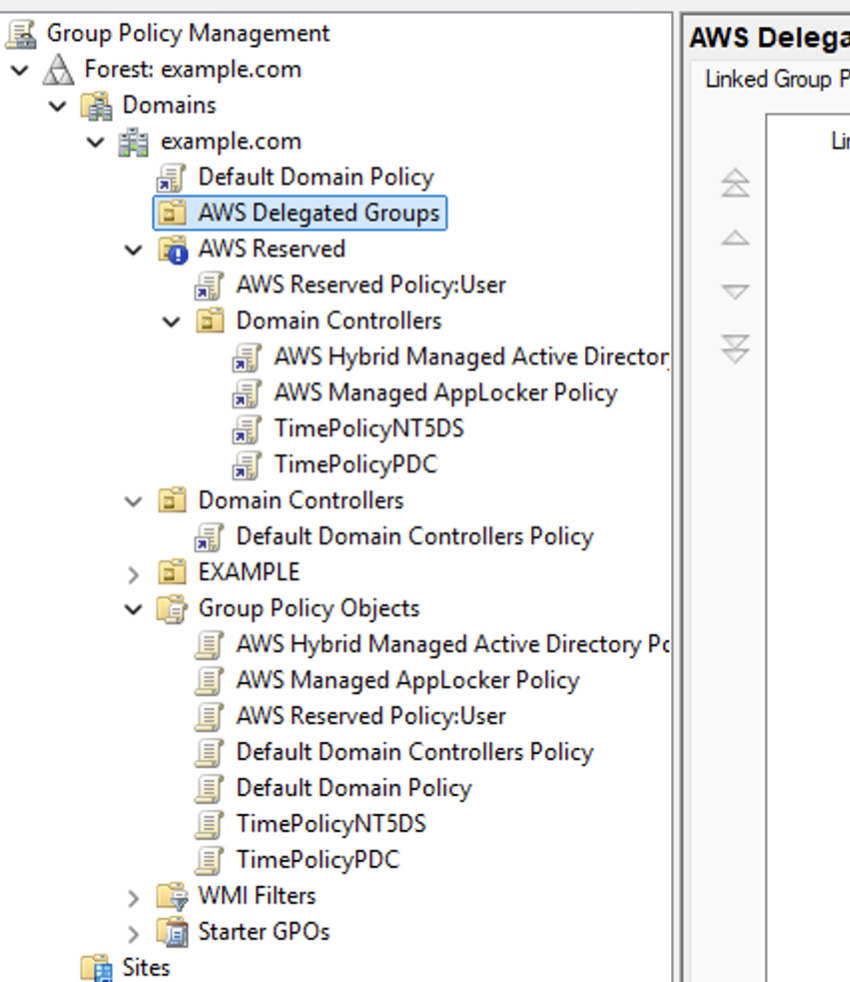
These new GPOs are designed to limit access/management of the AWS managed DCs. By using Kerberos Constrained Delegation, the setup is able to prevent mangement of the AWS DCs and limit replication from only the two DCs assigned during the creation of the directory. Note also the inheritance blocking of GPOs at the AWS Reserved OU. Also, from my understanding these new AWS DCs are full-fledged DCs and not Read-Only.
A couple of notes on the setup/prep. The console requires the running of an “Assessment” that leverages two DCs that are configured with the System Manager client. The Assessment runs 48 different test to ensure the forest/domain meets the service’s requirements. Among these tests are:
Child Domain Test – This test looks at the AD forest topology and will fail if there is a child domain
Replication Test – Validates the repl status and ensures each DC is available for replication – my initial assessment failed due to the NTP setup. I had to run time command to point the PDC FSMO to AWS NTP: w32tm /config /manualpeerlist:"169.254.169.123" /syncfromflags:manual /reliable:YES /update
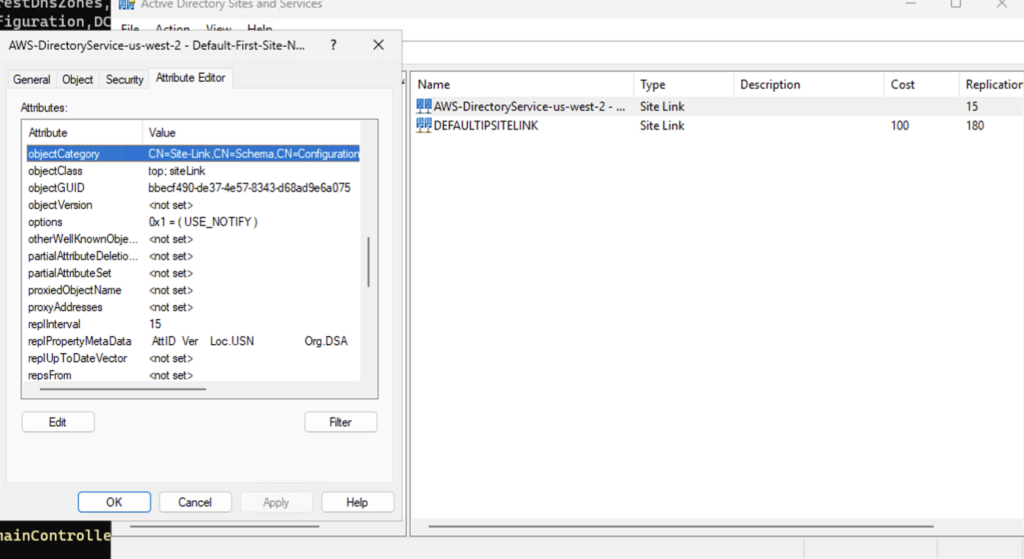
And speaking of replication, the new site is configured with “Change Notification” replication option enabled (note the options value below):
In the setup of the self-managed AD I choose functional forest/domain modes of 2016. The DCs that AWS use are running 2019 and so I doubt 2025 mode would be supported (may an update soon?).
In Summary
This is a very impressive setup the AWS Directory team has developed. It has a limited use case due to the requirment of a single-domain forest. I’ve not seen many enterprises with a single-domain model (but I’ve been out of the AD space for some time). I guess the team would be working on an update to support more complex forest/domain topologies.
The assessment testing is very thorough and can expose some limitations/issues of an Active Directory. I’d love to take a peek at the code these tests run, my guess is there’s a lot of PowerShell goodness there.
I hope you find this helpful…and Happy Building.
